- Home
- Security, Compliance, and Identity
- Microsoft Defender Vulnerability Management Blog
- Leverage advanced hunting to better understand your discovered devices
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Microsoft Defender For Endpoint’s device discovery capabilities provide the opportunity to better understand which devices exist on your corporate network and the ability to protect your estate by improving your posture.
We have all heard of instances, such as the NASA breach using a Raspberry Pi device, where attackers physically breached an environment, insert a device that’s connected to the network, and then use the device to exercise malicious activity. For more flexibility and additional discover capabilities, Microsoft offers advanced hunting, a query-based threat hunting tool within M365 Defender to help you gain more visibility into managed and unmanaged devices, along with vulnerability data via Microsoft Defender Vulnerability Management.
With advanced hunting, users can access queries to return data for specific scenarios, such as finding unfamiliar devices or devices in a specific subnet. Several queries are available in our advanced hunting community today and new queries will continue to be added when available.
In this blog post, we will show a few queries you can use to address various use cases to find devices as well as the ability to create custom alerts in your network.
Find devices within a subnet
Use the query below to help find devices that were discovered on a specific subnet in your network (Replace the values “IpV4Range” or “IpV6Range” with the value you are searching for):
let IpV6Range = “2001:4898::1050:1050/127”;
DeviceNetworkInfo
| where Timestamp > ago(7d)
| summarize arg_max(Timestamp, *) by DeviceId
| mv-expand IPAddressEntry=todynamic(IPAddresses)
| extend IPAddress=tostring(IPAddressEntry.IPAddress)
| where ipv6_is_match(IPAddress, IpV6Range)
let IpV4Range = “172.22.138.0/24”;
DeviceNetworkInfo
| where Timestamp > ago(7d)
| summarize arg_max(Timestamp, *) by DeviceId
| mv-expand IPAddressEntry=todynamic(IPAddresses)
| extend IPAddress=tostring(IPAddressEntry.IPAddress)
| where ipv4_is_in_range(IPAddress, IpV4Range)
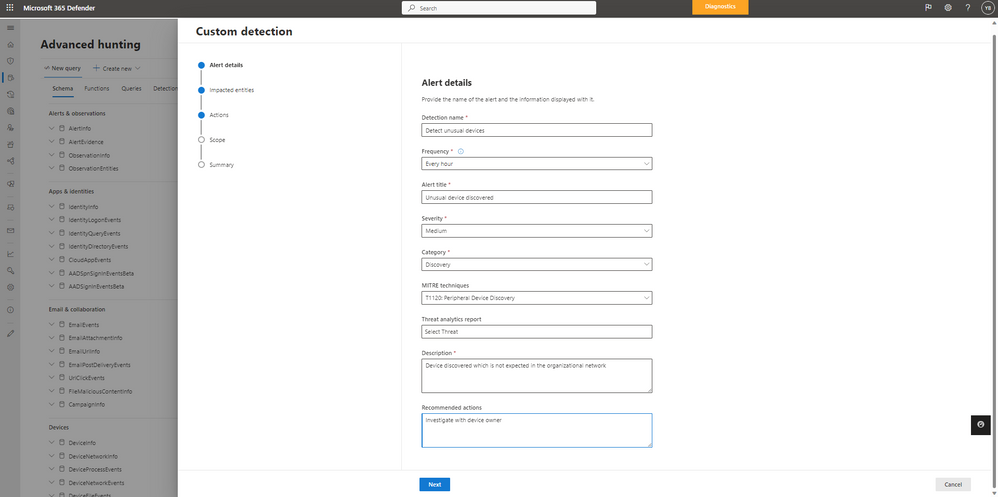
Once you have the query, you can then create the custom detection rules to run on whatever subnet you wish to monitor. Custom detection rules let you proactively monitor various events and system states, including suspected breach activity and misconfigured endpoints. You can set them to run at regular intervals, generating alerts and taking response actions whenever there are matches.
You can also create additional custom detections rules to generate alerts for other scenarios important to you.
Find devices that you can better protect by onboarding them to MDE
There may be devices on your network Microsoft Defender for Endpoint can support but for some reason, they were not onboarded to Defender for Endpoint. Onboarding these devices will ensure that they are better protected and have detection and response capabilities as well as vulnerability assessments. Run the following query to understand which of your devices can be onboarded:
DeviceInfo
| summarize arg_max(Timestamp, *) by DeviceId
| where OnboardingStatus == "Can be onboarded"
Find devices by specific type or subtype
To find which devices exist in your corporate network by type of device (i.e. router), you can use the following query:
DeviceInfo
| summarize arg_max(Timestamp, *) by DeviceId
| where DeviceType == "NetworkDevice" and DeviceSubtype == "Router"
You can change the values of “DeviceType” or “DeviceSubtype” to other types of devices.
Find devices with a prefix or suffix in the host name
If you manage your devices with a specific naming convention, you can query devices based on names as well with the below queries. Change the values after “startswith” or “endswith” accordingly:
// Prefix
DeviceInfo
| summarize arg_max(Timestamp, *) by DeviceId
| where OnboardingStatus != "Onboarded"
| where DeviceName startswith "minint"
// Suffix
DeviceInfo
| summarize arg_max(Timestamp, *) by DeviceId
| where OnboardingStatus != "Onboarded"
| where DeviceName endswith "-pc"
Find rare device models
To find rare models of devices, leveraging the following query:
DeviceInfo
| summarize arg_max(Timestamp, *) by DeviceId
| summarize ModelCount=dcount(DeviceId) by Model
| where ModelCount < 5
Generate alerts on discovered devices
Advanced hunting for device discovery isn’t only used to proactively hunt for devices that are sitting static but can also be leveraged to generate custom alerts. For example, if you need to protect internet facing assets that attackers may be seen as a prime target to exploit or have certain assets on VLAN or subnet that you may want to monitor more closely, you can tag these assets with advanced hunting’s machine tags.
How to get started?
For more information about advanced hunting, read more here.
For detailed information on this capability and more queries, please visit the community
Learn more about Microsoft Defender Vulnerability Management here.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.