- Home
- Security, Compliance, and Identity
- Microsoft Defender Threat Intelligence Blog
- Using MDTI with the Diamond Model for Threat Intelligence
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Cybersecurity incidents can be complex and challenging to investigate, requiring advanced tools and techniques to identify the scope of the attack, determine the adversary's tactics and procedures, and develop an effective response strategy. Microsoft Defender Threat Intelligence (MDTI) provides robust tools and features that enable security analysts to quickly investigate incidents and respond to cyber threats by applying the Diamond Model for Intrusion Analysis Framework to threat intelligence.
The Diamond Model is a framework for understanding cyber threats that was first introduced by Sergio Caltagirone, Andrew Pendergast, and Christopher Betz in 2012 to improve the analysis of cyber intrusions. With the unique intelligence in MDTI, security professionals can easily use The Diamond Model to understand adversaries, uncover threat infrastructure, and quickly and resolutely respond to security incidents.
The Diamond Model is based on the idea that a cyber threat is not just a single event but a complex interaction between four different entities. The first is the adversary, or the individual or group that is responsible for the attack. The second, the infrastructure, is the adversary's tools and resources they use to carry out the attack. Third is the capability, i.e., the skills and knowledge of the adversary. Finally, the victim is the organization or individual that is targeted by the attack. Together, these entities make up the four corners of the Diamond Model.
The Diamond Model dissects incidents to help responders understand and mitigate an incident. Conversely, the Diamond Model for Threat Intelligence takes a broader lens, aggregating multiple intrusions to discern patterns and the evolution of threat actors. This broader perspective is more strategic, emphasizing predicting future threat actions and understanding adversaries' overarching motivations and intents.
By organizing and analyzing data related to these four core tenants, the Diamond Model provides a more comprehensive understanding of the threat landscape, enabling security analysts to develop more effective response strategies and better protect their organizations against cyber threats.
Identifying the adversary is an important step in any cyber investigation. In the case of a malicious IP address, it is essential to understand who is behind the attack and their motives. With Microsoft Defender Threat Intelligence, we can quickly search for information about the IP address and identify any known threat actors or associated groups.
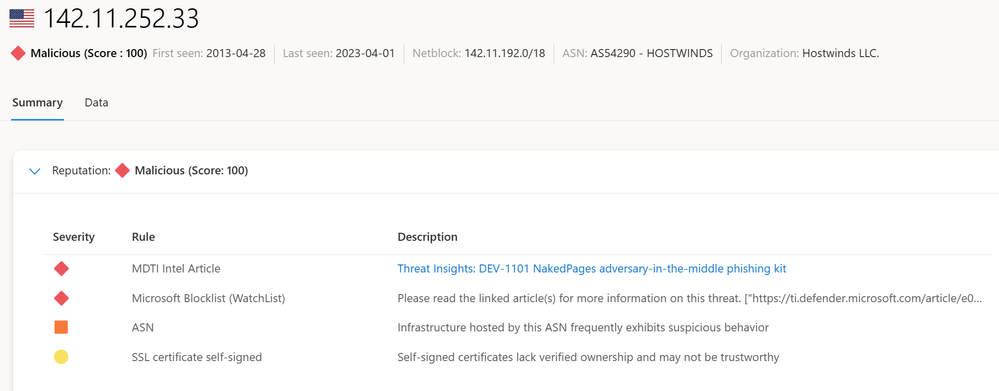
For example, during an investigation we have detected a potential attack coming from the IP address 142.11.252[.]33. From the screenshot below, we can see that the IP address has a "Malicious" reputation with a score of 100. We can also see that there is a threat intelligence article that an analyst can use to conduct further research on this potential adversary.
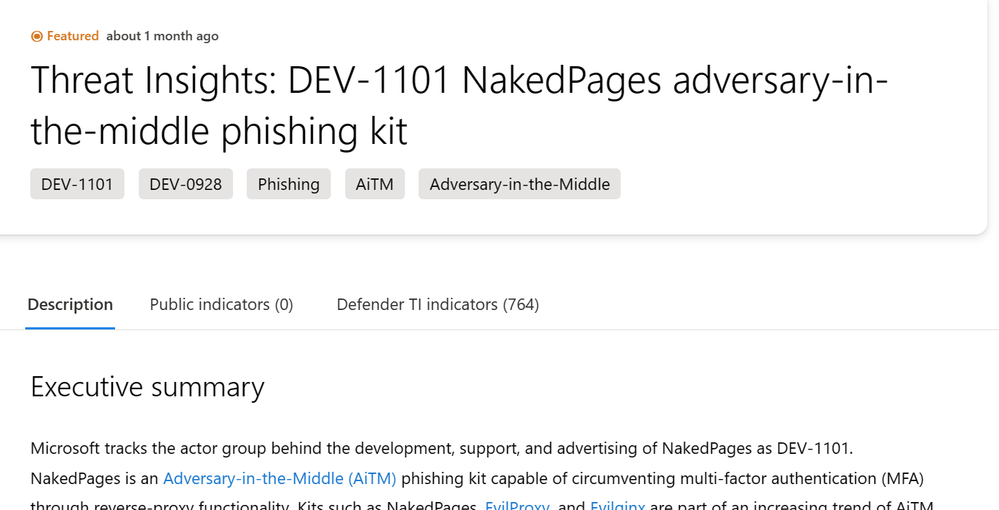
The link in the description is pivotal. When clicked, it presents the threat intelligence article. The article includes several pages summarizing the activity being reported, as well as 764 MDTI indicators.
In the screen shot below, we can see some of the indicators that were listed in the article:
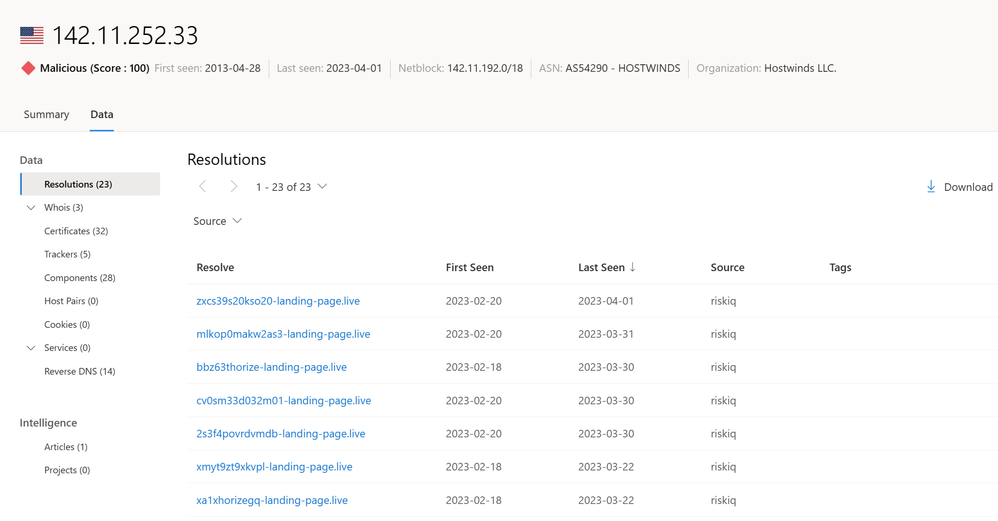
In addition to identifying the adversary, it is also important to understand the infrastructure being used in the attack. This may include identifying other IP addresses, domains, or websites that are being used to carry out the attack.
Using a technique called Infrastructure Chaining, we can map out the different components of the infrastructure that an adversary has been known to use. This includes identifying additional IP Addresses, Domain Names, Host Pairs, and other data sets that are provided by MDTI. This will allow an analyst to have a better understanding of other artifacts to search for on their network. Additionally, by understanding the infrastructure used by the adversary, the organization can better develop a more targeted and effective response strategy.
Another important factor to consider is the victim of the attack. By analyzing the victim's systems and data, we can identify any vulnerabilities or weaknesses that may have been exploited by the attacker and take steps to prevent similar attacks in the future. This can be done using vulnerabilities scanners within the organizations network and using Microsoft External Attack Surface Management (MDEASM) for devices that are Internet facing.
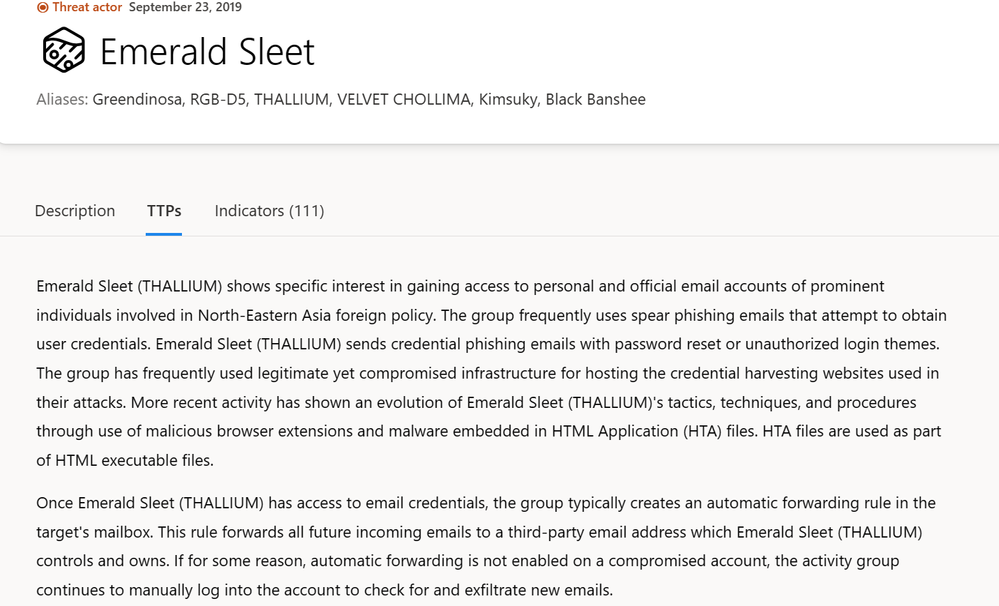
It is important to identify the specific capabilities being employed by the adversary. This may include identifying the malware being used, the specific techniques being employed, and the tools and resources being utilized. If an adversary is well known, we can utilize MDTI Intel Profiles to provide additional information about that adversary. This would include their known tools, tactics, and procedures (TTPs).
Additionally, if researchers at Microsoft have identified any related malware that an adversary is using or specific MITRE ATT&CK techniques, that information is also available in Intel Profiles.
In conclusion, the Diamond Model is a valuable tool for understanding cyber threats and the danger those threats pose to your own organization. By understanding the four corners of the diamond, analysts can gain a deeper understanding of the adversary, their methods, and capabilities. This information can then be used to develop effective mitigation strategies and protect your organization from attack.
Here are some key takeaways from the blog post:
- The Diamond Model is a framework for understanding cyber threats.
- The model has four main components: adversary, infrastructure, capability, and victim.
- Each corner of the diamond should be analyzed to understand the threat.
- The Diamond Model can be used to develop effective mitigation strategies.
- Microsoft Defender Threat Intelligence is a best-in-class solution to develop intelligence to populate the four corners of the Diamond Model.
Questions?
We hope you found this blog helpful in understanding the value Defender TI can provide. If you have inquiries regarding threat intelligence, use cases mentioned or not mentioned in this blog and are not currently working with a Defender TI Technical Specialist or Global Black Belt, please email mdti-pm@microsoft.com.
Feedback?
We would love to hear your ideas to improve our MDTI platform or where our threat intelligence could be used elsewhere across the Microsoft Security ecosystem or other security third-party applications. Feel free to email mdti-pm@microsoft.com to share that feedback as well. If you are currently working with a Defender TI Technical Specialist or Global Black Belt through this PoC, please communicate your requested use cases and product feedback to them directly.
Learn About New Microsoft Defender Threat Intelligence Features!
Please join our Cloud Security Private Community if you're not a member and follow our MDTI Private & Public Preview events in our MS Defender TI channel. You will not have access to this Teams channel until you are a Cloud Security Private Community member. Users that would like to help influence the direction/strategy of our Defender TI product are encouraged to sign up for our Private Preview events. Those participating will earn credit for the respective Microsoft product badges delivered by Credly.
We want to hear from you!
Be sure to join our fast-growing community of security pros and experts to provide product feedback and suggestions and start conversations about how Defender TI is helping your team stay on top of threats. With an open dialogue, we can create a safer internet together. Learn more about MDTI and contact sales to try it today.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.