- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint Blog
- Announcing a streamlined device connectivity experience for Microsoft Defender for Endpoint
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Update: The streamlined device connectivity experience is generally available as of 5/8/2024.
Deploying new security services can be an uphill battle. In the past, engineering teams looking to establish connectivity between endpoints and Defender for Endpoint services had to configure their firewalls and proxies using a more granular list of URLs. Some network devices required the use of static IPs to achieve the same goal. Once deployment was completed, the configured URLs needed to be maintained in case new services were introduced.
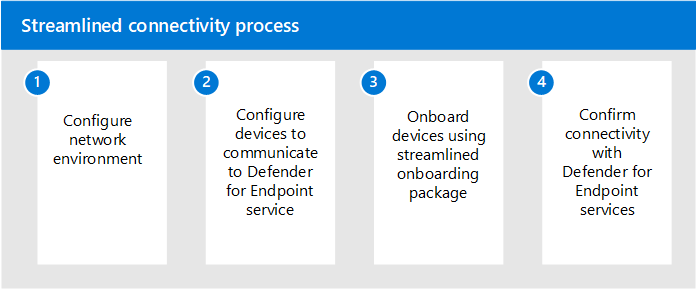
To help simplify device connectivity and management, we are excited to announce a new method that streamlines the device connectivity and onboarding experience for Microsoft Defender for Endpoint.
This new experience makes it easier for security teams to configure and manage Microsoft Defender for Endpoint services by reducing the number of URLs required to connect to cloud services during onboarding, expanding network configuration options to support IPs, and simplifying post-deployment network management.
Defender for Endpoint streamlines device connectivity for security teams by:
- Reducing the Defender for Endpoint URL set by more than 60%
- Offering the option to use static Defender for Endpoint-dedicated IP ranges instead of URLs when configuring their network environments
- Adding support for Defender for Endpoint Azure service tags
- Extending Defender for Endpoint client analyzer to support testing this new connectivity method in both pre & post-onboarding scenarios
Note: To use the new streamlined connectivity method, devices will need to onboard or migrate to Defender for Endpoint using an updated onboarding package. Learn more about onboarding and configuring your network environment.
Reducing the URL set
Before, security teams needed to separately configure and manage each of the following services in their networks. This would include updating their network for any new services. Under this solution, any future Defender for Endpoint services will be consolidated under the simplified domain – eliminating the need for security admin to make adjustments.
Under the new streamlined onboarding experience, the Defender for Endpoint-recognized simplified domain *.endpoint.security.microsoft.com will consolidate and replace URLs for the following core Defender for Endpoint services:
- Cloud-delivered protection (MAPS)
- Malware sample submission storage
- Automated investigation and remediation sample storage
- Defender for Endpoint command and control
- Endpoint detection and response cyber data
Expanding network configuration options
Previously, the absence of dedicated IPs made configuring Defender for Endpoint more challenging for environments using older firewalls devices without hostname resolution or wildcard support.
For more flexibility across diverse network environments, we now offer an alternative to URLs. Security teams can use static IP ranges that are dedicated to Defender for Endpoint or subscribe to the Azure service tag. – minimizing the complexity of frequent updates to network security rules. Learn more about Azure virtual network service tags.
Remaining services required for connectivity
With the new streamlined experience, most of the individual required URLs for Defender for Endpoint services will no longer be required for connectivity. These individual URLs will be funneled into a consolidated URL (and resolved to IP ranges).
Some required services, like those core to Windows and managing updates, are not included in the URL consolidation, therefore remains to be configured separately. Learn more about the new Defender for Endpoint required URL list.
Note: To align with Defender for Endpoint security and compliance standards, data will be processed and stored in accordance with the tenant's physical location. Based on client location, traffic may flow through different Azure datacenter regions. For more information, see Microsoft Defender for Endpoint data storage and privacy | Microsoft Learn.
Prerequisites
To use the new streamlined onboarding experience, devices must meet specific prerequisites. Please make sure each device meets the minimum operating system, Windows KB, and antivirus version requirements before proceeding:
Note: Devices running on the Microsoft Monitoring Agent (MMA) agent will need to continue onboarding using the MMA method and its corresponding required URL set. Windows devices running RS1 through RS4 can use the streamlined onboarding experience but will require a longer list of URLs.
Applicable licenses
- Microsoft Defender for Endpoint Plan 1
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender for Business
- Microsoft Defender Vulnerability Management
Operating Systems
- Windows 10 version 1809+
- Windows 11
- Windows Server 2019
- Windows Server 2022
- Windows Server 2012 R2, Server 2016 R2, fully updated running Defender for Endpoint modern unified solution (installation through MSI).
- MacOS and Linux supported releases running product version 101.2309+ on Insider Fast (Beta).
Windows Minimum Component Versions:
- Microsoft Defender Antimalware client: 4.18.2211.5
- Microsoft Defender Engine: 1.1.19900.2
- Microsoft Antivirus (Security Intelligence): 1.391.345.0
- Minimum Windows KB/Sense version: >10.8040.*/ March 8th 2022+ (see table in public documentation)
MacOS/Linux Minimum Component Version:
- 101.24022.*+ version
Onboarding and migration
After confirming your devices meet the prerequisites, make sure that your network environment is properly configured to support the new streamlined onboarding experience. The new streamlined experience enables you to configure your network with either the consolidated domain or IPs. Learn more about configuring network connectivity.
Once your network and devices are updated to communicate with the required destinations, begin the device onboarding or migration process.
Note: Make sure to confirm successful connectivity with Defender for Endpoint services before moving forward.
The end-user experience or how Defender for Endpoint functions on a device will not change. Only the URLs or IPs that a device uses to connect to the service will change.
For devices already onboarded to Defender for Endpoint using the standard method that wish to migrate to the streamlined onboarding method, run the ‘streamlined’ package on the device and reboot the device. Once rebooted, the device should automatically switch over to the new experience. For most operating systems, device offboarding is not required to migrate. During migrations, device ID’s are retained and there is no loss of data history.
For information on migrating devices already onboarded to Defender for Endpoint, see migrating devices to use the streamlined connectivity method.
The streamlined onboarding package can be found in the M365D Defender portal under Settings > Endpoint > Onboarding alongside the standard onboarding approach. To get started, follow the instructions here.
Things to know before you begin
- The streamlined onboarding experience is currently not supported via APIs. This includes Microsoft Defender for Cloud and Microsoft Intune.
- The new streamlined onboarding experience has specific prerequisites that do not apply to the standard onboarding experience. Please make sure your devices meet the prerequisites before continuing.
Learn more
Looking to learn more about the new streamlined onboarding experience? For more details, see:
- Onboarding devices using streamlined connectivity for Microsoft Defender for Endpoint | Microsoft Le...
- Migrate devices to use the streamlined onboarding method | Microsoft Learn
- Configure your network environment to ensure connectivity with Defender for Endpoint service | Micro...
Let us know what you think!
We are excited to share a more streamlined approach to device onboarding with you and your security teams. Let us know what you think in in the comments below. We take all feedback into consideration as we work to enhance your security experience with Microsoft Defender for Endpoint.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.